An Academic Cyber Range
Tectonic is a cyber range designed to provide realistic cybersecurity scenarios for education and training through the deployment of networks, systems and applications that can be used to train users on cybersecurity topics. Key functionalities include customizable network configurations, real-time monitoring and automated attack simulations.
It incorporates existing tools from the infrastructure as code (IaC) approach, which allows for the specification of all the components of a cybersecurity scenario in a declarative manner. This specification is made in a high-level language that can be interpreted and allows for the automatic generation of scenarios on the laboratory underlying platform. Declarative descriptions of the scenarios make them easily versioned, maintained, and shared, facilitating collaboration with other institutions and laboratories of this type.
The following figure illustrates various components of the cyber range solution, the technologies used in the implementation, and the different use cases carried out by student users and instructors. The components are organized in five layers, each fulfilling a particular function in the platform's operation.
The underlying infrastructure constitutes the real-world infrastructure on which the systems and networks that form the basis of a particular scenario are deployed. Currently deployments on the AWS cloud or on-premises using Libvirt are supported, with more planned.
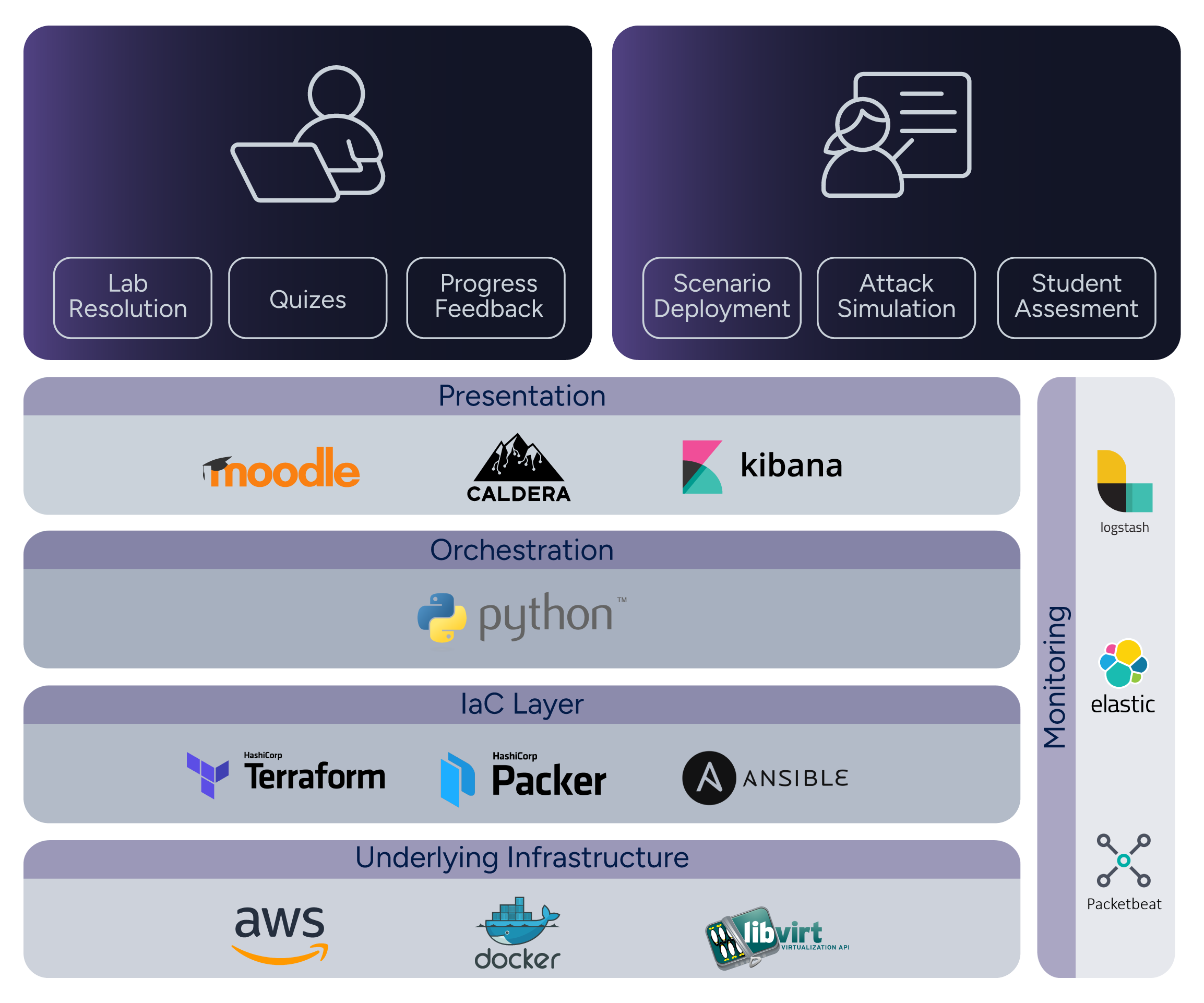
To achieve the deployment of the infrastructure in an automated manner, Infrastructure as Code (IaC) tools are used, such as Packer, Terraform and Ansible. These tools manage the resources to be deployed and the configurations to be applied to them. Ansible playbooks, in particular, are extensively used for configuration.
A Python component orchestrates these tools and manages the life cycle of the scenarios, including their deployment, elimination, powering on, powering off, and listing information. The scenarios themselves are described by a specification that allows users to declare various aspects, such as the machines to be deployed, the networks used to connect them, and the configurations to be applied to the machines, among others.

Projects and Activities
Methods and tools for adaptive and certified cybersecurity
The objective of this research program is to continue working on lines already explored and to explore new aspects in the following complementary research domains: (1) conception and development of automated mechanisms for the analysis and prevention of computer attacks on web applications and computer systemsbased on machine and deep learning techniques, model-driven security and process mining, (2) development of methodologies and tools that allow setting up a Cyber Range that becomes an advanced platform for education, training, experimentation, and research around the multiple aspects of cybersecurity and (3) develop, adapt and specializemethods, techniques, and tools for the formal verification o f smart contracts, protocols and computing platforms based on cryptocurrencies.
Regarding the cybersecurity training platform, work will be done on developing and implementing a new platform (of the cyber range type)for cybersecurity training. The platform will allow the different actors (teachers, trainers, students, professionals, andresearchers) to define, execute, experiment, and resolve cybersecurity scenarios. It shall also allow the managementand monitoring of courses and training programs.
Team: Gustavo Betarte, Daniel Calegari, Juan Diego Campo, Guillermo Guerrero, Carlos Luna, Rodrigo Martínez, Fernanda Molina, Álvaro Pardo, Amanda Riverol, Marcelo Rodríguez, Felipe Zipitría.
Funding: Partially funded by a grant provided by the program CSIC Grupos I+D 2023-2026.



Tectonic DFIR Workshop (Ciberlac)
This workshop took place in August 29th 2025, and was conducted as part of the 1st Summer School on Cybersecurity, organized by Ciberlac in Mexico City, Mexico. The main objective of this activity was to provide high-quality practical training to students, contribute to the development of new talent in the field of cybersecurity, and foster a collaborative environment among universities in the Latin America and Caribbean region. The Tectonic workshop is designed for students to develop competencies in incident response and digital forensics. The activity was mainly practical, where 61 participants of 17 universities of Latin American and the Caribbean were provided with a simulated organizational network and had to respond to a cybersecurity incident affecting the infrastructure.
Team: Gustavo Betarte, Juan Diego Campo, Guillermo Guerrero, Rodrigo Martínez
Funding: Partially funded by a grant provided by the program CSIC Grupos I+D 2023-2026 and Banco Interamericano de Desarrollo.




Train The Trainers in Tectonic (Ciberlac, Red Clara)
This workshop took place in November 29th 2024, and was organized by Ciberlac, Red Clara and the Tectonic team. The main objective of this activity was to begin creating an academic community of Cyber Range instructors who can contribute to the development of the tool, generate a collaborative repository of scenarios, and generally contribute to cybersecurity training in the region. The Train the Trainers workshop is designed for participants to get to know Tectonic and become familiar with the operation of this cyber range, training them so that they can adopt it for creating and delivering new cybersecurity scenario trainings. The activity was mainly practical, where participants had an example scenario in Tectonic and could experiment with creating and specifying new ones.
Team: Gustavo Betarte, Juan Diego Campo, Guillermo Guerrero, Rodrigo Martínez
Funding: Partially funded by a grant provided by the program CSIC Grupos I+D 2023-2026 and Banco Interamericano de Desarrollo.





Train The Trainers in Tectonic (JUCC)
This workshop took place in December 16th 2024, and was organized by the Grupo de Seguridad Informática (GSI) in the context of the Jornadas Uruguayas de Ciencias de la Computación (JUCC). The main objective of this activity was to begin creating an academic community of Cyber Range instructors in the Uruguayan academic and professional cybersecurity community who can contribute to the development of the tool, generate a collaborative repository of scenarios, and generally contribute to cybersecurity training in the region. The Train the Trainers workshop is designed for participants to get to know Tectonic and become familiar with the operation of this cyber range, training them so that they can adopt it for creating and delivering new cybersecurity scenario trainings. The activity was mainly practical, where participants had an example scenario in Tectonic and could experiment with creating and specifying new ones.
Team: Gustavo Betarte, Juan Diego Campo, Guillermo Guerrero
Funding: Partially funded by a grant provided by the program CSIC Grupos I+D 2023-2026.



Tectonic team
Gustavo Betarte, Juan Diego Campo, Guillermo Guerrero, Rodrigo Martínez, Marcelo Rodríguez, Felipe Zipitría.

Gustavo
Betarte
Gustavo Betarte received a BSc degree in Computer Engineering (1990) from Facultad de Ingeniería de la Universidad de la República, Uruguay (FING-Udelar), and a MSc. (1993) and a PhD. (1998) in Computing Science from the University of Gothenburg, Sweden. He is a Full Professor of the Department of Computer Science (InCo) and principal researcher and head of the Computer Security team (GSI) of FING-Udelar. Dr. Betarte is member of the Uruguayan Researchers National System (SNI, Level II) and an active researcher (Grado 5) of the Informatics Area of PEDECIBA. Since 2006 he is the Technical Director of the Computer Security Consulting Team of Tilsor SA, an Uruguayan IT company.
His research interests include formal methods, program verification, software and system security and foundations of computer science. He is currently working on the application of knowledge discovery techniques for adaptive software security, the formal definition and verification of security properties of critical systems and the design and implementation of cyber ranges. For more detailed information please check the full CV and DBLP list of publications.

Juan Diego
Campo
Juan Diego Campo received a BSc degree in Computer Engineering (2009) from Facultad de Ingeniería de la Universidad de la República, Uruguay (FING-Udelar), and a PhD. (2016) in Computing Science from PEDECIBA Informática, Uruguay. He is an Assistant Professor at the Department of Computer Science (InCo) and member of the Computer Security team (GSI) of FING-Udelar. Dr. Campo is an active researcher (Grado 3) of the Informatics Area of PEDECIBA.
His research interests include formal methods, program verification, software and system security and foundations of computer science. He is currently working on the application of knowledge discovery techniques for adaptive software security and the security of cyber-physical systems. For more detailed information please see the DBLP list of publications.

Guillermo
Guerrero
Guillermo Guerrero received a BSc degree in Computer Engineering (2021) from Facultad de Ingeniería de la Universidad de la República, Uruguay (FING-Udelar), and a MSc. in Computing Science (2025) from PEDECIBA Informática, Uruguay. He is a teaching assistant of the Department of Computer Science (InCo) and member of the Computer Security team (GSI) of FING-Udelar. He has worked as an IT security consultant at Tilsor since 2021.
His research interests include cyber range platforms and the application of process mining techniques for the assessment of cyber range trainings.

Rodrigo
Martínez
Rodrigo Martinez received a BSc degree in Computer Engineering (2009) from Facultad de Ingeniería de la Universidad de la República, Uruguay (FING-Udelar), and a MSc. (2019) in Computing Science from PEDECIBA Informática, Uruguay. He is an Assistant Professor at the Department of Computer Science (InCo) and member of the Computer Security team (GSI) of FING-Udelar. He has worked as an IT security consultant at Tilsor SA since 2009 and is a member of the company's Incident Response Team (CSIRT-Tilsor). Since 2018 he is the technical leader of the computer security team of Tilsor.
His research interests include application and web application security and the use of machine learning techniques applied to web application security. For more detailed information please check the full CV.

Marcelo
Rodríguez
Marcelo Rodríguez received a BSc degree in Computer Engineering (2007) from Facultad de Ingeniería de la Universidad de la República, Uruguay. He is currently studying Master in Computing Science of PEDECIBA Informática, Uruguay. He is an Assistant Professor at the Department of Computer Science (InCo) and member of the Computer Security team (GSI) of FING-Udelar. He has worked as an IT security consultant at Tilsor since 2009 and is a member of the company's Incident Response Team (CSIRT-Tilsor). Research interests include attacker profiling in cybersecurity, digital forensics analysis and the development of methodologies and tools for correlation of threats indicators.

Felipe
Zipitría
Felipe Zipitria received a BSc degree in Computer Engineering (1999) from Facultad de Ingeniería de la Universidad de la República, Uruguay (FING-Udelar), and a MSc. (2008) in Computing Science from PEDECIBA Informática, Uruguay. He is an Assistant Professor at the Department of Computer Science (InCo) and member of the Computer Security team (GSI) of FING-Udelar.

Publications and Dissemination Activities
Articles in Journals and Conferences
G. Guerrero, G. Betarte, J. D. Campo, Assessment of Red and Blue Team Training in the Cyber Range Tectonic using Process Mining. CLEI Electronic Journal Vol. 28 No. 5 (2025): Regular Papers and CLEI 2024 best papers (part 2). 2025.
Link to PDF
G. Guerrero, G. Betarte, J. D. Campo, Process Mining-Based Assessment of Cyber Range Trainings. L Latin American Computer Conference (CLEI). 2024.
Link to PDF
G. Guerrero, G. Betarte, J. D. Campo, Tectonic: An Academic Cyber Range. 2024 IEEE Biennial Congress of Argentina (ARGENCON). 2024.
Link to PDF
Theses
Master theses
G. Guerrero, Aplicación de minería de procesos para la evaluación de entrenamientos ofensivos y defensivos en ciberseguridad, Master Thesis, Pedeciba Informática. 2025.
Link to PDF
Graduate theses
N. Vidal, F. Correa, Emulación de Dispositivos Android en un Cyber Range, Computer Engineer, Facultad de Ingeniería, Universidad de la República (Uruguay). 2025.
Link to PDF
G. Corujo, M. Rodríguez, CyRa.uy : Hacia un cyber range académico, Computer Engineer, Facultad de Ingeniería, Universidad de la República (Uruguay). 2023.
Link to PDF
R. Gallardo, G. Guerrero, Reingeniería del Laboratorio de Seguridad Informática: análisis, diseño e implementación de un Cyber Range, Computer Engineer, Facultad de Ingeniería, Universidad de la República (Uruguay). 2021.
Link to PDF
Invited Talks
J. D. Campo, Tectonic: un Cyber Range Académico, Congreso Internacional de Informática, Electrónica y Comunicación (CIIECOM), Panamá, 2025.
J. D. Campo, Tectonic: un Cyber Range Académico, Jornadas Uruguayas de Ciencias de la Computación (JUCC), Uruguay, 2024.
G. Betarte, J. D. Campo, Tectonic: un Cyber Range Académico, Congreso Nacional de Ciencias de la Computación Bolivia (CCBOL), Bolivia, 2024.
J. D. Campo, Tectonic: un Cyber Range Académico, OWASP AppSec Río de la Plata, Uruguay, 2024.
J. D. Campo, Plataformas de Entrenamiento en Ciberseguridad, Conferencia Latinoamericana en Informática (CLEI) - Workshoop de Cibserseguridad de Ciberlac, Bolivia, 2023.

